The recent attacks on computer networks at health locations in Britain, Russia’s interior ministry, the Spanish telecom giant Telefonica and the US delivery firm FedEx, as well as organisations in Sweden, Germany and around the world has once again raised the issue of cyber security.
Railway control and information systems are becoming more connected, and are therefore exposed to cyber-attacks. In other industries, businesses attacks on critical infrastructures have emerged as serious and disruptive threats. Tailor-made trojans and malware have appeared that can sabotage, collect information, or hold organisations to ransom.
The latest software attacks exploited a flaw in the Windows XP operating system exposed in documents leaked from the US National Security Agency. A technique known as ransomware locks users’ files unless they pay the attackers a designated sum in the virtual currency Bitcoin.
But, on this occasion, did it affect rail, and what are the risks?
Understandably rail operators do not want to divulge too much about their risks and defences, but it would appear that rail in the UK did not suffer any successful cyber-attacks; at least this time. A Network Rail spokesperson said: “Safety is our top priority, which is why we work closely with government, the security services, our partners and suppliers in the rail industry and security specialists to combat cyber threats. Our security is constantly under review, but we can’t discuss the details for obvious reasons.”
It was reported that Manchester Metro had been compromised, but the system failure experienced was not due to a cyber-attack. Instead, it was down to a “major technical issue”. Danny Vaughan, head of Metrolink at Transport for Greater Manchester, said: “There was a technical systems failure which affected communications between the control room and trams out on the network.” All services were halted and trams returned slowly to their depots.
Metrolink runs a closed IT network with high levels of security and there was no indication of any form of hacking or cyber attack which would also result in shutting down the system.
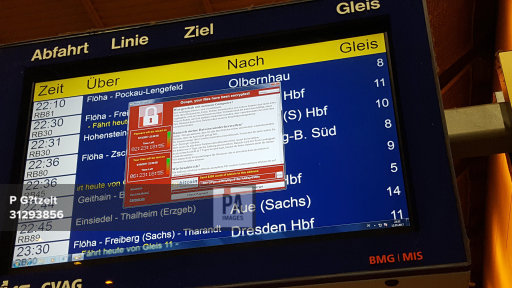
However, in Germany, Deutsche Bahn (DB) computers were impacted, with the company reporting that display panels in the stations were affected. Travellers tweeted pictures of hijacked departure boards showing the ransom demand instead of train times. Despite this, DB insisted that trains ran as normal.
In many cases the UK railway control systems predate commercial computer systems and are not networked, or they are relatively new and have robust cyber security measures in place. Rail has also benefited from the relativity slow implementation of networked control systems and has learned from other control system industries on the requirements for security measures.
Rail must not be complacent though. More attacks on critical infrastructures are being detected around the world. The loss of service or the damage to customer and public confidence can have dramatic consequences. Critical infrastructures include health, emergency services, energy, financial services, food, government, water and transport.
Project Honeytrain
To determine how attacks on such critical infrastructures could be performed and how widespread the hacking community is, British-based computer security firm Sophos, in cooperation with Koramis of Germany, created project Honeytrain. A model was set up as a honeypot to hackers of a mythical virtual rail transport control and operating system, in order to gain information about the quality, quantity and aggressiveness of possible attacks.
The project was not specifically intended to assess the risks to rail, but was chosen as it was easier to model rail than other industrial control systems.
A virtual rail infrastructure was reproduced with real hardware including computer systems and communication protocols. Software components of automation and control systems (such as existing railway systems), and CCTV videos of real stations and train operator workstations were simulated. A mythical customised website with general information, timetables, ticketing and information about train disruption was also created. Logins and passwords were left at their defaults and no security measures were enabled. To hackers around the world, though, it appeared to be a real railway.
A compromised gateway to the internet was established with multiple analysis tools for logging and reporting, including a network sniffer and an intrusion detection system. The analysis tools were specially designed for the requirements of control systems. Based on up-to-date provider databases and a geolocator, countries were assigned to the IP addresses used for the attacks.
For each control system, a public IP address was assigned. This reflected that many real industrial systems can be accessed through digital connections. The integration of video streams from stations and drivers’ cabs completed the holistic image of a realistic control system. Throughout the duration of the project, the network traffic as well as system events were all recorded.
Results
The infrastructure of the Honeytrain project was in operation for only six weeks and, in total, 2,745,267 attacks were identified. Many of these would be generated by hacking software and the number doesn’t represent the number of individual hackers, although the number of hackers was significant. At least one attempted attack was detected from almost every country in the world. The ten ‘worst’ countries, in order of attempted attacks were:
- China 41%
- USA 9%
- France 7%
- Poland 4%
- Moldova 3%
- Taiwan 2%
- UK 2%
- Turkey 2%
- Russia 1%
- Germany 1%
- Rest of the world 28%.
The majority (61 per cent) of attempted attacks occurred on the media server and firewall components. One possible reason could have been the open standard services of these systems and the availability of out-of-the-box attacks offered by hacking tools. In contrast, the industrial component vulnerabilities and attack routes are known, but they are not always implemented (yet) in hacking tools.
Analysis of attempted attacks revealed that the majority were carried out as automated dictionary attacks. In a dictionary attack, the hacker is trying to identify an unknown password using a dictionary list. Often whole dictionaries as well as known or commonly successful combinations are used to create such a list.
Four valid logins were detected, with two of them performed by dictionary attacks. The other two valid logins were (according to the IP address of the attacker) not based on dictionary attacks. It is assumed that one or both attackers repeatedly accessed the login to access the system. By geolocation of the last resolvable IP address, the first and second dictionary attack could be identified as carried out in either Japan or China.
In one of the attacks the command line was started, two PINGs were executed, and the execution programme opened. It was found that the security configuration of industrial components was read out via a central tool, and the settings were exported. As a result, it was possible to activate the front lights of one mythical train.
At the same time as the attack, it was observed that the same accessing IP address tried to control a mythical signal using another dictionary attack. However, this attack was not successful. The sequence of attacks shows that the attacker had a deep knowledge of the industrial control systems used for the Honeytrain project. The actions were not performed randomly, but deliberately.
Another attack was on the media server. Using a dictionary attack, the valid login credentials were determined and the aim of this attack was to change the content on the website. Singapore was identified as the origin.
Cross-industry strategy
The good news is that, as a result of the analysis of the results, it was concluded that relatively small measures (for example robust passwords and firewalls) are sufficient to prevent unauthorised access to railway systems, or to avoid their visibility within the internet.
These measures, and many more, are included within the GB rail cross-industry cyber security strategy. The strategy was instigated by the Department for Transport (DfT) and the National Cyber Security Centre (NCSC) and produced by RSSB. Complying with the strategy will ensure the rail industry is better prepared for cyber threats and will be ready for new legislation being introduced regarding cyber security for critical infrastructure.
The strategy supports the vision and the Rail Technical Strategy objective that all information and control systems must be resilient to cyber-attacks (RTS, 2012), while not limiting innovation in the railway. The strategy was handed to Rail Delivery Group in December 2016 for its onward development, including guidance, support and monitoring of its delivery.
Thanks to Dave Robson, principal consultant at SNC-Lavalin, for his assistance with this article.
This article was written by Paul Darlington.